Grid Posts Widget – 3 Columns – Category : General
Page 1 of 1
Grid Posts Widget – 5 Columns – Most Viewed
Page 1 of 7





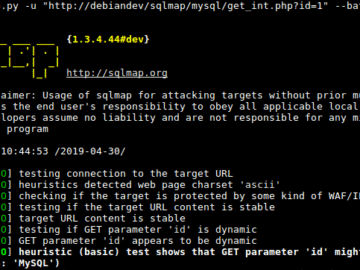










 Daily practice and real-time application is key to perfection
Daily practice and real-time application is key to perfection
Recent Comments