
This time, however, we are doing it on bare metal, making the process much simpler and more efficient.
🕵️♂️ Offensive Google framework. Contribute to mxrch/GHunt development by creating an account on GitHub.
The first step involves downloading and installing the requirements necessary for the successful operation of Ghunt. You can copy and paste these commands one by one directly into your terminal:
sudo apt install pipx
pipx ensurepath
pipx install ghunt

While the above packages are being installed, you can go ahead and install the Ghunt browser extension by mxrch in your browser.

After all the packages are done installed and Ghunt is successfully installed, we can proceed with logging by:
ghunt login
It will then ask for cookies. Remember to use your unofficial or unimportant Google account to log in to the GHunt browser extension. After logging in, it will take you to a page with two options. Simply copy the Base64-encoded cookies and paste them into your terminal after selecting the second option, which says “Manually paste Base64-encoded authentication.”

Paste the copied based64 cookies below:

Then, it will proceed to authenticate after you press Enter.

Now, that the hard part is over, we can move on to the fun part. Go ahead and type the following command in a fresh terminal:
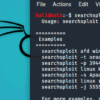
ghunt -h

Now, to simply search an email you can type this directly on your terminal and it will start generating outputs:
ghunt email <email_address> --json user_data.json
Something like this:


As you can see, we’ve gained access to very critical information such as the Google user ID, Google Chat data, reviews, and Google Maps data. With a bit more aggressive OSINT using geo-search, this information can even reveal a person’s location — and if the person is not cybersecurity-aware, it might also expose their phone number. Since this is my personal Gmail account, I’ve kept most of the sensitive data private. However, if someone isn’t careful, this kind of exposure can cause serious damage. So, please use this article and the information it contains responsibly, and do not engage in any illegal activities.
I hope you enjoy this article. Stay with me to get more interesting articles on cybersecurity and always !












 Daily practice and real-time application is key to perfection
Daily practice and real-time application is key to perfection